Compliance Management
Make compliance your next revenue driver
Map every action to compliance controls and frameworks to reduce risk and deliver measurable progress that keeps clients audit-ready - and coming back.


Benefits

Always be audit ready
Quickly identify control gaps, map them to frameworks, and generate client-ready audit reports in just a few clicks.

Support every framework
Track compliance across NIST, HIPAA, PCI-DSS, CIS, and more - all from one centralized dashboard.

Demonstrate progress and value
Automatically link scans and findings to specific controls to show measurable improvement and risk reduction over time.
“Cyrisma - A Swiss Army Knife for Client Security and Compliance.”
Features and Solutions
Align risk and remediation to specific control sets.
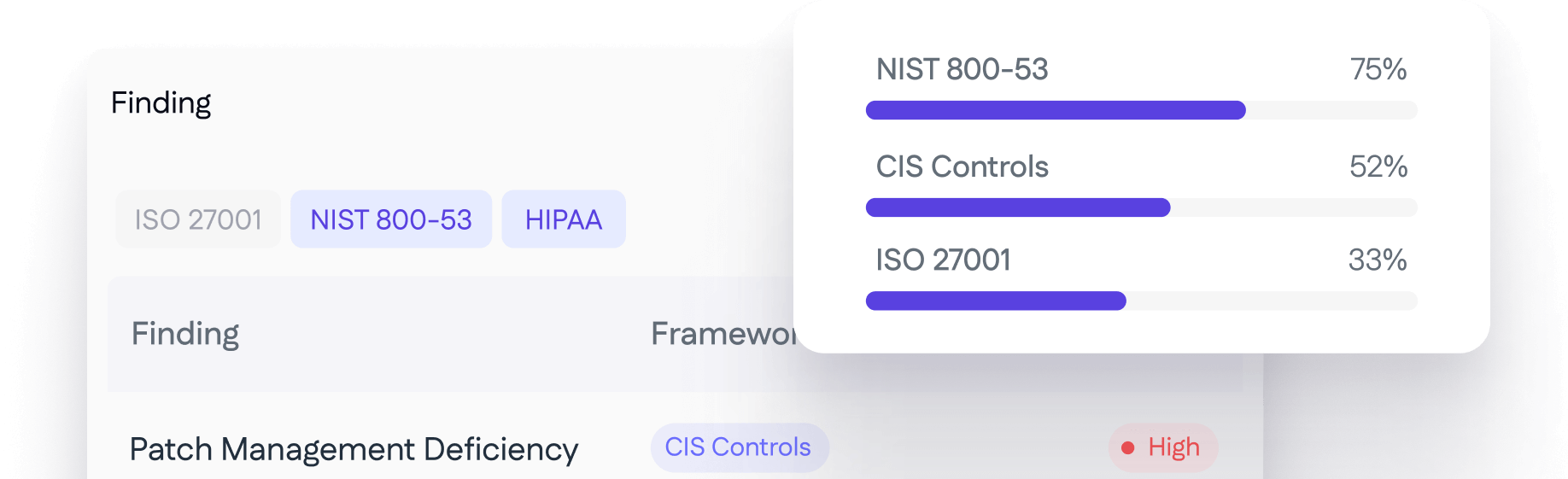
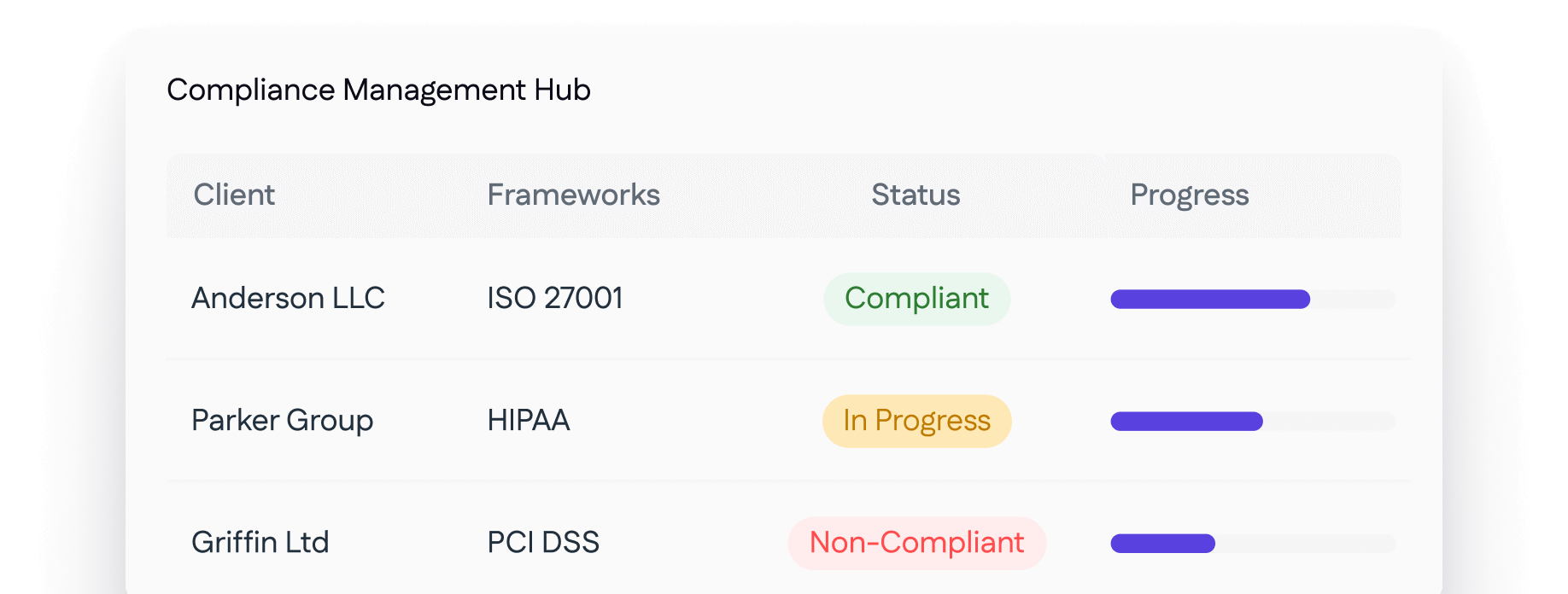
Use the multi-tenant model to support dozens and hundreds of clients with ease.
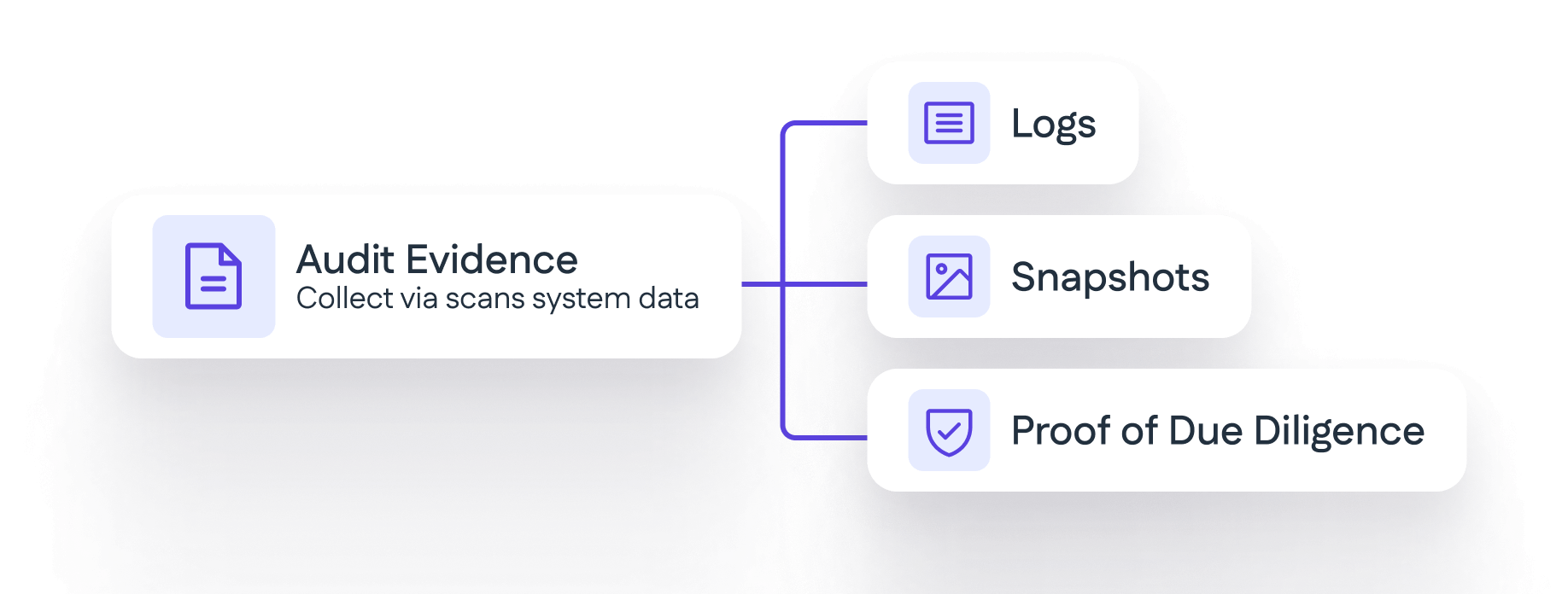
Collect and map audit evidence using Cyrisma’s scans and system data, and retain snapshots, logs, and proof of due diligence for audits or insurers.
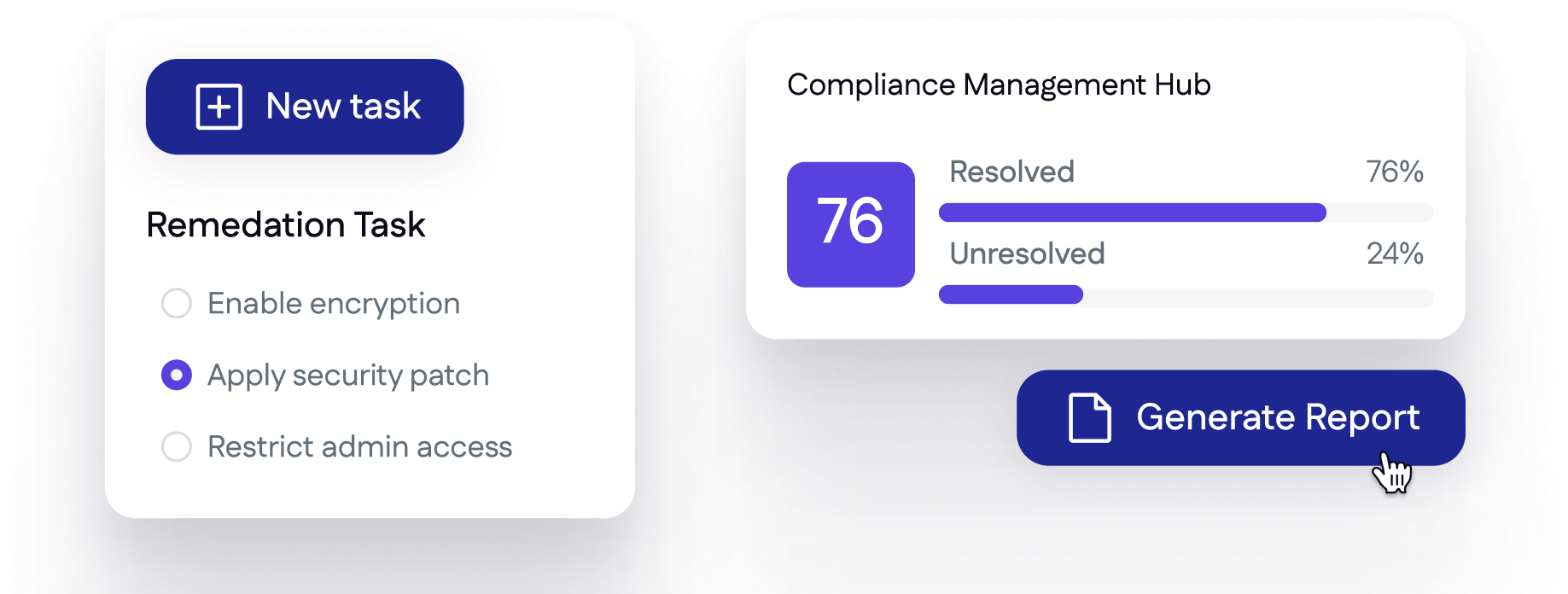
Connect actions and remediations directly to compliance outcomes and deliver white-labeled scorecards that demonstrate compliance readiness in minutes.
Make Compliance a Competitive Edge
It helps you monitor, manage, and demonstrate compliance with frameworks like NIST, HIPAA, PCI-DSS, CIS, and more. You get real-time visibility into your posture, track remediation efforts, and generate audit-ready reports.
The platform maps findings (like vulnerabilities or data exposure) to specific controls within your chosen framework. You can view compliance scores, control status, and historical trends from a centralized dashboard.
Cyrisma supports more than 20 common standards and regulatory frameworks including NIST, HIPAA, CMMC, PCI-DSS, ISO/IEC 27001, CIS Benchmarks, and custom GRC frameworks based on your needs.
Yes. Cyrisma includes exportable compliance scorecards, remediation logs, and executive summary reports - designed for auditors, leadership teams, and client QBRs.
Absolutely. Findings are linked directly to remediation steps. You can assign tasks, track progress, and show improvement over time—closing the loop between discovery and compliance documentation.
Compliance status updates in near real time based on new scan results, configuration changes, or data discovery findings—keeping your posture accurate and current.
Yes. The multi-tenant design, built-in frameworks, and reporting tools make Cyrisma a perfect fit for MSPs delivering compliance services or vCISO offerings to clients.



