The unified platform to identify and mitigate cyber risk
Don’t wait for a breach to take action. Ensure your customers are secured and resilient in the face of evolving cyber threats.

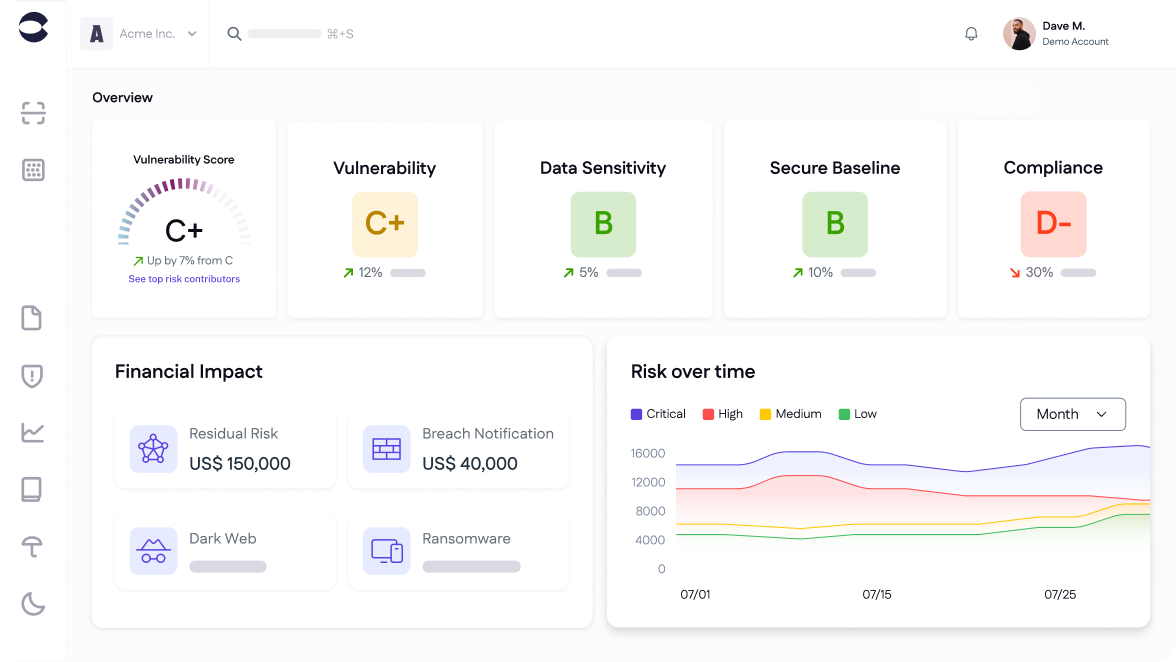

Ensure business resilience
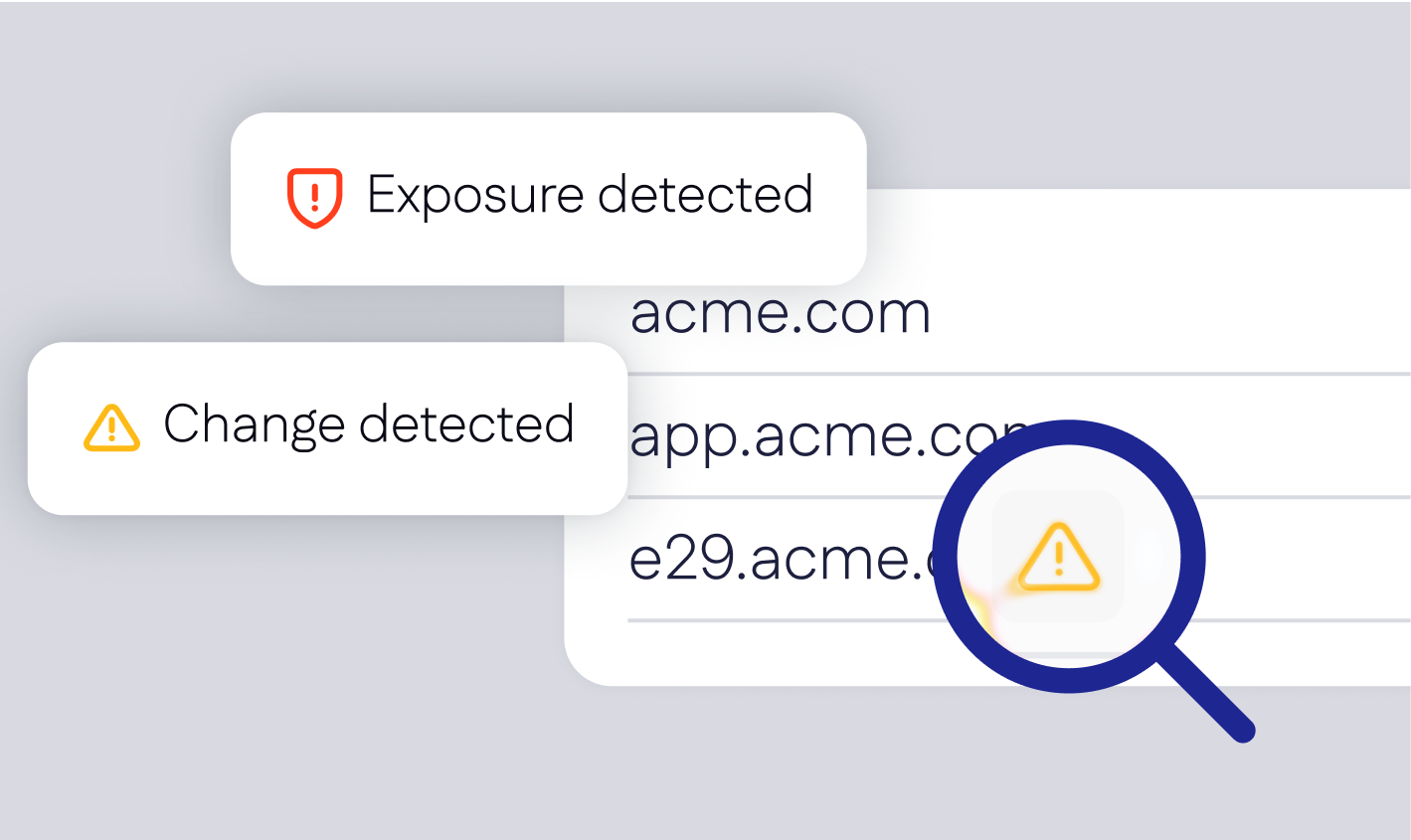
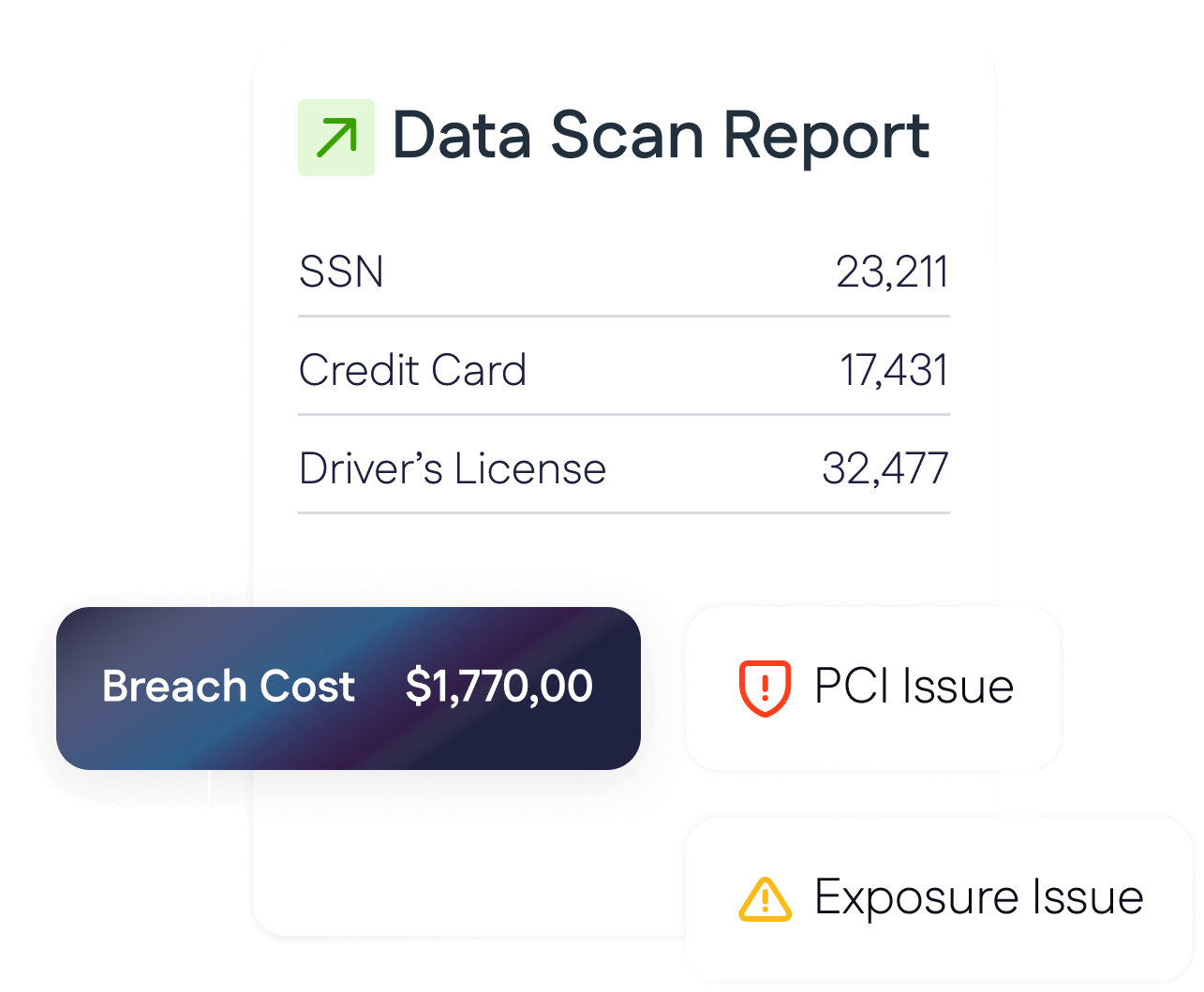
Discover the attack surface
What are the points of attack from an attacker’s perspective?
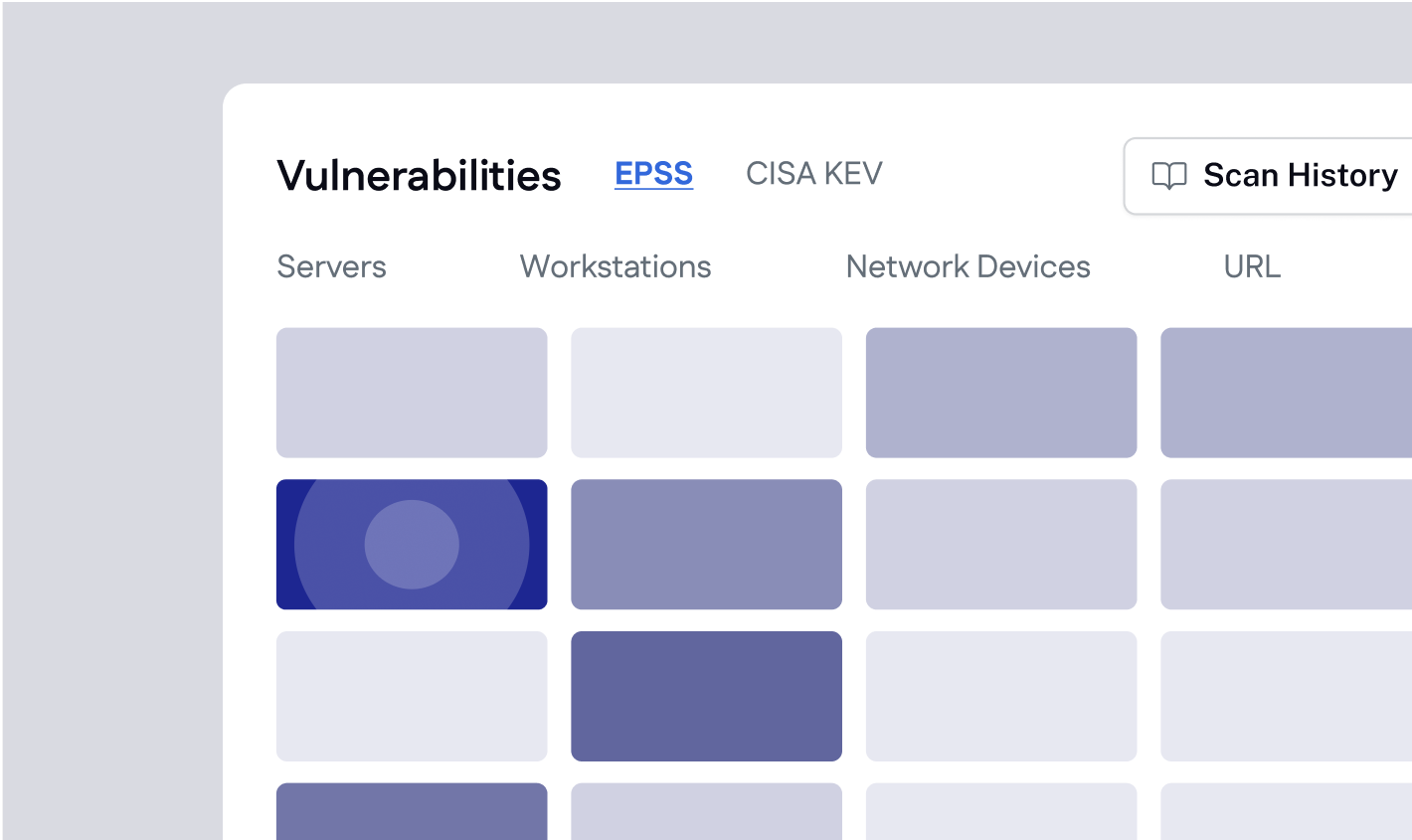
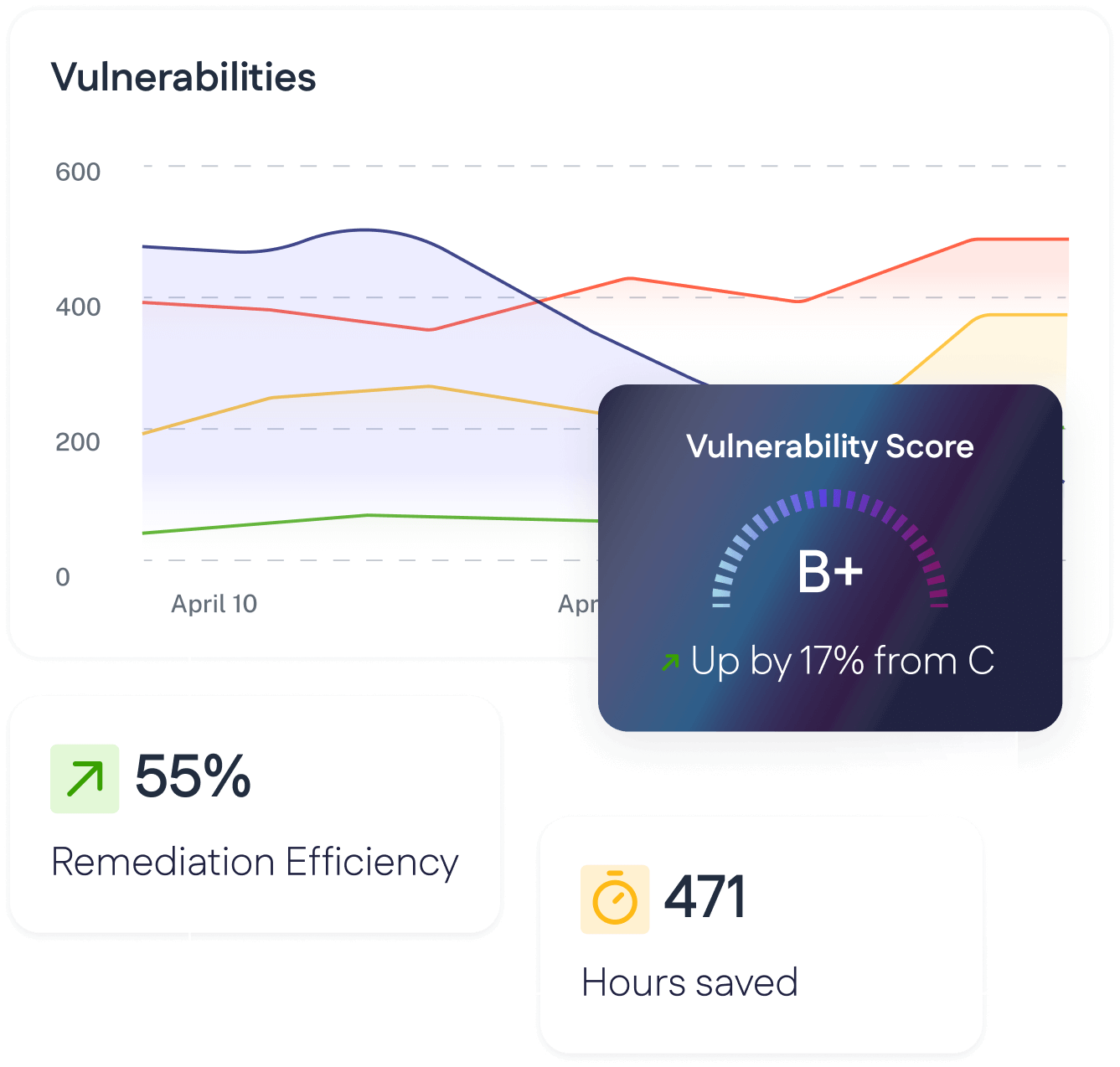
Prioritize the gaps
What are the weakest points threatening my business continuity?
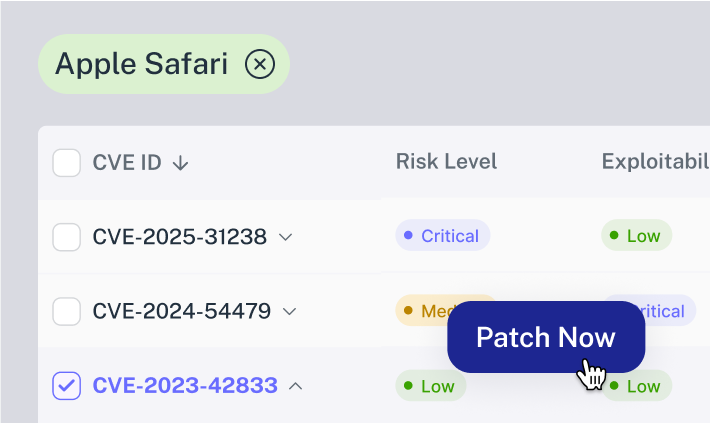
Remediate vulnerabilities
How can I best harden my security, given limited time resources?
Cover every angle



We scale with you for every stage of growth
.png)
Drive net new security revenue with powerful prospecting and reporting features to rapidly surface insights and demonstrate to prospects and customers alike.
Expand your security offering and reduce total cost of ownership by consolidating tools and offering new value-add services to your customers.
Drive margin expansion and operating efficiency with business automations for scanning, monitoring, and remediating. Optimize for your techs' and SOC analysts' time by only surfacing actionable insights and next steps.
Loved by partners







Cyrisma by the numbers
Turn risk into revenue with Cyrisma
Get a DemoFrequently asked questions

Activities performed in Cyrisma map automatically to common frameworks such as CIS v8, HIPAA, PCI-DSS, and ISO 27001, along with supporting external evidence and documentation to prepare comprehensive, audit-ready scorecards and white-labeled client reports.

By surfacing actionable insights, simplifying operations, and automating remediations and reporting, Cyrisma helps partners scale their security offerings, expand margins, and increase customer retention.

Cyrisma unifies four key modules - Attack Surface Management, Vulnerability Management, Data Discovery, and Compliance Tracking - into a single dashboard, purpose-built for MSPs, MSSPs, and IT Teams.

Partners report an average 65% time savings by consolidating asset discovery, vulnerability scanning, patching, and compliance workflows into one platform, reducing tool sprawl and manual effort.

Yes - reports and dashboards can be branded with your logo, helping MSPs deliver security and compliance insights as their own managed service.

Yes. Cyrisma integrates with common PSA systems, such as ConnectWise, Halo PSA, Autotask, and more, enabling automation of ticketing and reporting - reducing overhead and ensuring total visibility across your managed environments.

Yes. Cyrisma is designed for MSPs managing multiple clients. You can easily segment, monitor, and report across tenants from one centralized dashboard.





